Antivirus software can detect malware in almost any part of your system, but one place where it can't is in the GPU memory. There's at least one GPU rootkit capable of hiding malware in the GPU memory, but mentions of a new tool have now emerged, and it seems it has already been sold to an undisclosed entity.
Six years ago, Team Jellyfish created what's believed to be the first GPU-based malware. Named JellyFish, this Linux-based GPU rootkit is the most well-known one out there, working as the foundation for other GPU rootkits. Now, a new GPU-based malware independent from Jellyfish has been spotted and sold to someone.
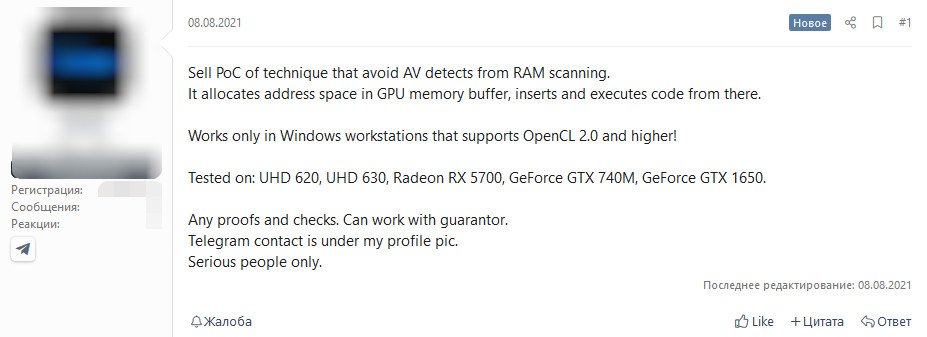
As reported by Bleeping Computer, recent activity on hacker forums shows that someone was selling a proof-of-concept technique that stores malware in the GPU memory buffer, rather than within RAM. This way, antivirus software that scans the RAM for malware won't be able to detect it.
Image credit: Bleeping Computer
The seller stated that this tool only works on Windows systems supporting Open CL 2.0 and above. The method was also tested in several GPUs, including Intel integrated graphics (UHD 620/630), the Nvidia GeForce GTX 740M and GTX 1650 and finally, the AMD Radeon RX 5700.
The tool has apparently already sold, and there are plans to demonstrate how it works publicly, according to vx-underground.
KitGuru says: Antivirus software developers and security researchers will no doubt be keeping an eye on this situation as it develops.
 KitGuru KitGuru.net – Tech News | Hardware News | Hardware Reviews | IOS | Mobile | Gaming | Graphics Cards
KitGuru KitGuru.net – Tech News | Hardware News | Hardware Reviews | IOS | Mobile | Gaming | Graphics Cards