Back in March Nvidia released its first GPU driver security patch of the year, addressing eight vulnerabilities found. Today, the next security update has begun rolling out, addressing an additional five recently discovered security flaws in the Windows drivers for GeForce, Quadro and Tesla graphics cards.
As always, it is encouraged that you update your drivers and software regularly to stay on top of security updates. The latest set of exploits only affect Windows-based systems, so Linux and macOS users don't necessarily have to worry.
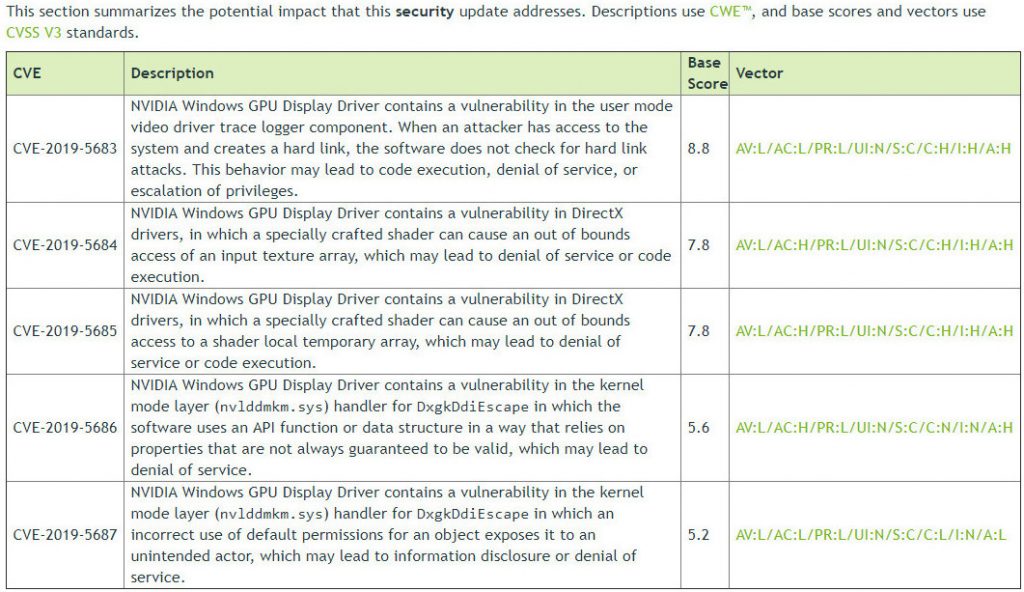
The image above details each of the vulnerabilities that have been fixed in this update, including a severity score. The biggest issue is CVE-2019-5683, which allows an attacker with local access to the system to avoid security detection for hard links, which can lead to running unauthorised code, denial of service attacks or an escalation of privileges
Other issues include two vulnerabilities in DirectX drivers and another two vulnerabilities found in the kernel mode layer, which could be exploited to avoid security protections and run denial of service attacks or rogue code.
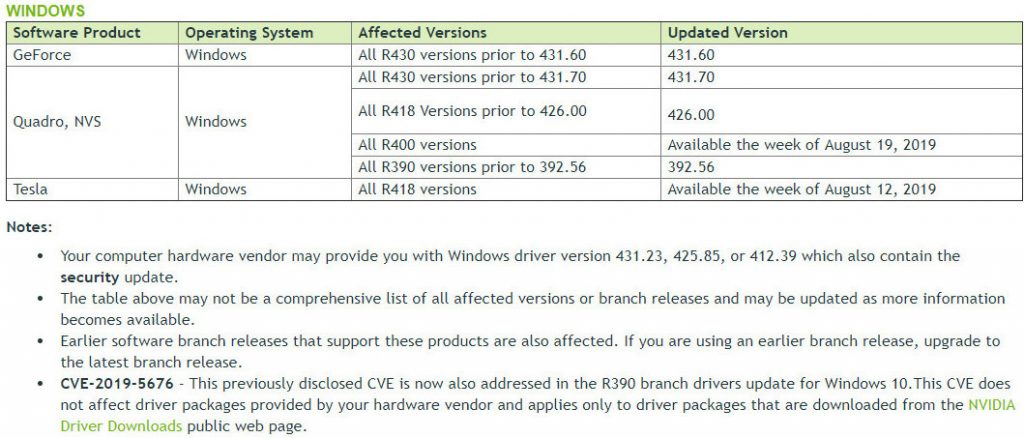
On the GeForce side, these issues are fixed in driver version 431.60, which has been available for about a week now. There are some more specific drivers for different Quadro/Tesla users, so be sure to check the image above to check which one you need.
KitGuru Says: If you haven't updated your graphics driver for a while, then now would be the time in order to stay on top of security updates.
 KitGuru KitGuru.net – Tech News | Hardware News | Hardware Reviews | IOS | Mobile | Gaming | Graphics Cards
KitGuru KitGuru.net – Tech News | Hardware News | Hardware Reviews | IOS | Mobile | Gaming | Graphics Cards